All Features

Jasmine Escalera
The traditional promise of work was simple: Support your life, care for your family, and build toward meaningful milestones like purchasing a home or saving for your children’s education. But for many modern professionals, that relationship with work is shifting. Instead of working to live, more…

Bruce Hamilton
In 1960, organizational psychologist Douglas McGregor introduced a conceptual framework of two contrasting theories about human motivation that grounded my Toyota Production System (TPS) learning.
His Theory X was based on the assumption that workers are fundamentally lazy and can’t be trusted to…

Adam Grant
Nano Tools for Leaders—a collaboration between Wharton Executive Education and Wharton’s Center for Leadership and Change Management—are fast, effective tools that you can learn and start using in less than 15 minutes, with the potential to significantly affect your success and the engagement and…

Megan Wallin-Kerth
Working with a disability can be a frustrating and isolating experience. As someone who spent years blaming vitamin deficiencies, anxiety, and even Covid for worrisome symptoms before finally seeing a neurologist—and then a movement disorder specialist, I can attest that even the lengthy process of…

Troy Harrison
What does onboarding mean? If you said “onboarding a salesperson” consists of doing the HR paperwork, giving a facility tour, a few days of shadowing existing salespeople, and then expecting the salesperson to hit the ground running, you’re not alone. Entirely too many sales managers feel that way—…

Akhilesh Gulati
A few months ago, during separate visits to an emergency department and an urgent care center, I experienced what many patients and clinicians now consider routine: long waits, crowded spaces, and visible strain on staff. It raised a familiar question that I’ve been asking for years: If the…
Adam Grabowski
Freedom is generally defined as the power or right to act, speak, or think as one wants without hindrance or restraint. The license to act as one pleases offers a host of benefits but can also produce consequences that limit your freedom. The same can be said of your manufacturing. The choices you…

Paige Orme, Maria DiBari
Capability maturity model integration (CMMI) is a process improvement framework required by many U.S. government contracts. If you’ve been through a CMMI appraisal in aerospace or federal contracting, you know there’s a typical pattern. Things look great on paper. Then the appraisal date gets…

Harish Jose
This article is inspired by the ideas of cybernetics, Martin Heidegger, and Nassim Taleb. I’m looking at what I think is the largest danger of large language models (LLMs).
LLMs are extraordinarily proficient in the domain of language, and that proficiency has quietly created a philosophical…

William A. Levinson
ISO 9001:2015 Clause 6.1 requires attention to actions to address risks and opportunities. There really is little practical difference between the two, as failure to exploit an opportunity constitutes a risk.
To put this in perspective, recall that poor quality is only the tip of the iceberg when…
Tzaferis Meleti
Let’s be honest. Conformity assessment has become dangerously comfortable. It’s familiar, structured, and predictable. It gives organizations a reassuring feeling of control because it produces clean documentation, tidy checklists, and audit reports that look professional. It also creates an…

Stephanie Ojeda
Integrating environmental, health, and safety (EHS) with quality management is no longer optional for manufacturers; it’s essential for achieving operational excellence, ensuring ISO compliance, and driving sustainable growth. Traditionally, EHS management and quality management systems (QMS)…

Donald J. Wheeler
Most data in business and industry belong to the category known as observational data. These data are the voice of your processes because they are the result of ordinary operations rather than an experiment.
Because the purpose of analysis is insight, the question is how to analyze observational…

Gleb Tsipursky
Organizations worldwide are navigating the transformative potential of generative AI (gen AI). But the key to unlocking its true value lies in human-centered implementation.
One of the most effective approaches to ensure success is to invite employees to participate in gen AI pilot programs. These…

Akhilesh Gulati
In the world of quality and lean, waste is the enemy. We hunt for it in cycle times, inventory buffers, and defects. But occasionally we encounter a form of waste so massive and literal that we fail to see it as a resource.
A recent redevelopment project at Denver’s National Western Center (NWC)…

Gary Howarth
In an emergency, knowing exactly where a first responder is can mean the difference between life and death. When a firefighter in a burning building fails to check in, how does the commander know where to look for them?
Public safety agencies face daily challenges in finding first responders…

AMPS Supply
Many warehouses consider peak season (November and December) as a finish line. Once peak season is over, demand stabilizes, pressure eases, and management immediately shifts its focus to the next planning cycle.
However, the period after peak season isn’t the epilogue but rather a transition that…

Manfred Kets de Vries
We often imagine the lives of our paleolithic ancestors as an unrelenting struggle. But the very existence of cave art suggests that at least some of them could focus on making meaning beyond necessity. So what drove them? Was it sacred ritual, primitive science, or early performance art? It might…

Quality Digest, Steve Ilmrud
Maintaining a skilled team from the bottom up is essential. But as skilled workers retire and take their knowledge with them, we rely more on a clear understanding of how digital and AI tools may be reshaping our approach to manufacturing quality, supply chains, and building a team. To provide some…

Chip Bell
Walk the aisles of any liquor store in the U.S., and brands named after people call for your notice—Johnnie Walker, Jose Cuervo, Captain Morgan, and Jim Beam. Perhaps the most revered name among them is Jack Daniel. Established in 1875, Jack Daniel’s Whiskey comes from the oldest distillery in the…

Dave Gilson
Creating a superhuman artificial intelligence could lead to two worst-case scenarios, says Charles Jones, a professor of economics at Stanford Graduate School of Business. In the first, the power to kill everyone—in, say, the form of an AI-engineered supervirus—could fall into the wrong hands. In…

ISO
Data are the backbone of our digital world. From healthcare to finance, and from government agencies to private businesses, organizations everywhere rely on vast amounts of data to function effectively.
It’s not just businesses that generate data. We all leave digital trails through our…

George Schuetz
Thickness is one of the most frequently measured dimensions, and one that’s very easy to understand. So, you might think that someone would come up with a one-style-fits-all measurement approach that’s good for just about every kind of thickness application. But it just isn’t so.
There are many…

X-Rite
The Pantone Color of the Year 2026, PANTONE 11-4201 Cloud Dancer, is described as an airy, billowy white that opens space for creativity, quiet reflection, and calm. A white that is both warm and cool, its serene presence symbolizes the need for clarity in a noisy world.
As soon as the choice was…
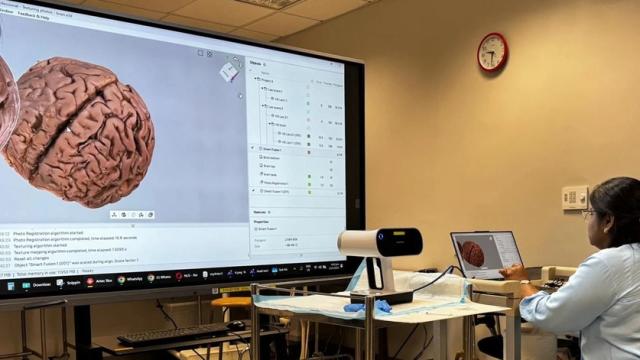
Paul Hanaphy
In the medical field, 3D technology is fast becoming indispensable. Whether used for educating patients ahead of surgeries or teaching students how to do these operations, anatomy models, both 3D printed and digital, offer an ideal solution for visualization ahead of time.
One of the main…