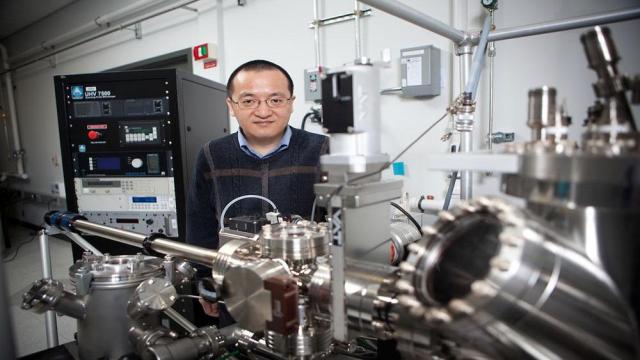
Most metals found in nature are actually in their oxide forms. To extract those metals to use in critical applications—ranging from infrastructure such as bridges and buildings to advanced technologies like airplanes, semiconductors, or even quantum materials—those oxides must be reduced with gases…
All Features
Donald J. Wheeler
Everybody wants to have good measurements. To this end, many recommend a regular schedule of recalibration. While this sounds reasonable, it can actually degrade the quality of the measurements.
The key to getting the most out of a measurement process is to know when to recalibrate and when to…

Jake Walton
Imagine you’re a student trying to pass a challenging class, one where the entire grade rests on the big test at the end of the semester. Fortunately, the professor handed out a syllabus that outlines exactly what will be on that final exam. Better still, you can also find a posted list of common…

Global Shop Solutions
Cutting costs is nothing new in manufacturing. What’s new is having to do it while juggling labor shortages, supplier delays, and tighter customer demands. Lean principles such as reducing waste and optimizing workflows still matter, but they’re no longer enough on their own. Staying competitive…

Sachin Waikar
Take two aspirin and call me in the morning: If only prescribing medications were as simple as that.
In reality, the prescription process involves many players and steps. Details must be accurately spelled out, interpreted, and double-checked to ensure patients get the correct drug and dosage.
“…

Dottie DeHart
Work-life balance is tough, and for most of us, it’s starting to feel like a thing of the past. Companies are demanding longer hours and increased productivity. Remote workers are being called back to the office, and the ones still at home are stuck in “always on” mode. With layoffs happening left…

Creaform
C hallenges abound for today’s manufacturers. Labor shortages and rising labor costs require innovative solutions to maintain productivity with fewer staff. Inflation continues to exert pressure on raw material costs, squeezing margins. Manufacturers are also racing against tight production…

Mike Figliuolo
After a couple of heart attacks, I’ve learned to eat much healthier. But finding snacks can be challenging once you remove Doritos and Cheetos from the equation. A good substitute for me is now Harvest Snaps, which are baked lentil pods. I highly recommend the tomato-basil version.
Anyway, I was…

ISO
Security configuration management (SCM) is a critical concern for organizations and a fundamental part of many cybersecurity frameworks. Consider this scenario: A team member tweaks a hardware setting on their personal laptop to boost software performance. However, this change causes unforeseen…

Susan Robertson
Productivity looks good on paper. It’s measurable, visible, and in many organizations, it’s worshipped. But here’s the problem: Productivity isn’t the same as progress.
Many cultures confuse motion with momentum. Leaders celebrate packed calendars, rapid responses, and efficiency hacks, but often…

Kamran Sayrafian
A few years ago, I heard on the news that many people were being hospitalized with a condition of excess fluid in the lungs, called pulmonary edema. It’s common in elderly patients. Pulmonary edema is dangerous and can lead to breathing difficulties and lung failure. Because it has the potential to…

Creaform
Karbonius Composites specializes in manufacturing precision molds and composite components across various sectors, including automotive restoration and high-performance customization. Founded in 2008 and based in La Coruña, Spain, the company’s production capabilities cover every step needed to…

Paul Hanaphy
The dental industry is seeing a surge in 3D printing, with the technology enabling a growing number of dentists to rapidly create custom implants in clinics around the world.
When it comes to customizing implants like dental crowns, bridges, guides, and aligners, 3D printing is faster, more…

Bruce Hamilton
Driving home from a customer last week, I caught a glimpse of a digital billboard—the kind that flashes eight different ads per minute. From a cost and aesthetic perspective, these backlit displays are a big step up from the old paperhanger versions. But I wondered: What do drivers actually see and…

Stephen Graham
Uncertainty often pushes manufacturers to slow down. Orders fluctuate, budgets tighten, and “wait and see” becomes the default strategy. But a growing number of companies are taking the opposite approach, using slowdowns as windows to invest in digitalization and automation.
Hexagon’s 2025 “…
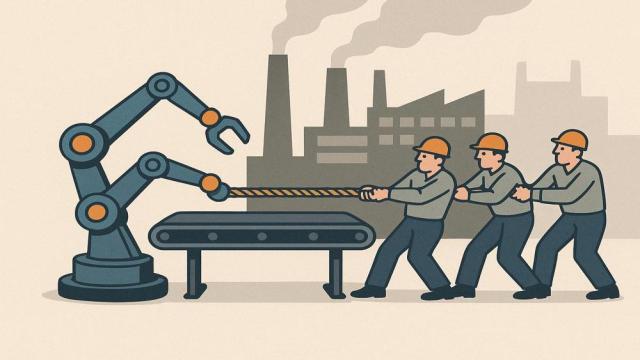
Kristin Burnham
Companies that adopt industrial artificial intelligence see productivity losses before longer-term gains, according to new research.
Organizations have long viewed artificial intelligence as a way to achieve productivity gains. But recent research about AI adoption at U.S. manufacturing firms…
Adam Zewe
A new theory-guided framework could help scientists probe the properties of new semiconductors for next-generation microelectronic devices or discover materials that boost the performance of quantum computers.
Research to develop new or better materials typically involves investigating properties…

CANEA
In several articles about challenges for tomorrow’s quality leaders, we’ve addressed how to plug the knowledge drain and effectively manage your company’s know-how. Your organizational structure and processes can be your worst enemy—or best asset. Organizational silos and roadblocks can impede…
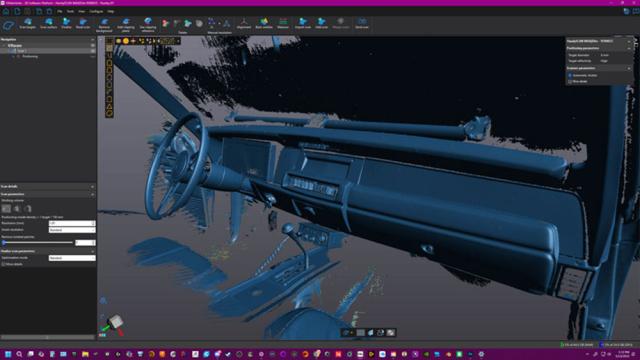
Creaform
Based in Tampa, Florida, Starr Creations, a powerhouse in fiberglass design and fabrication, is known for turning ambitious automotive visions into reality. Jesse Starr, creative director and 3D designer, founded the company with a passion for racing and innovation.
Starr Creations has been the…

Lexi Sharkov
They may seem simple, but SOPs (standard operating procedures) are surprisingly tricky. On the surface, they describe how a specific process is carried out at your organization. Pretty straightforward, right?
In reality, there are a lot of requirements for writing a good SOP, and auditors have a…

FOCO
Metal foundries are under intense pressure. Soaring energy bills now eat more than 30% of production budgets. Tough carbon regulations, such as the EU’s Carbon Border Adjustment Mechanism, reduce profit margins.
Foundries also struggle with costly scrap loss through melting and meeting tough…

Brookhaven National Laboratory
Chemists at the U.S. Department of Energy’s Brookhaven National Laboratory have designed a new way to convert abundant carbon dioxide (CO2) into formate (HCO2-), an industrial chemical used as a fuel, as an antibacterial/antifungal agent, and for making pharmaceuticals. Their reaction uses a light-…
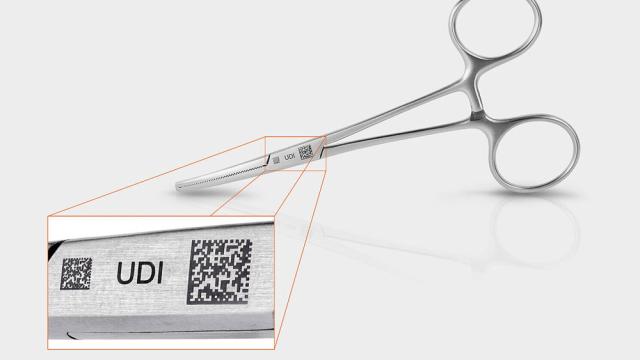
FOBA
In medical technology, safety is paramount. Every step in the manufacturing process must meet the highest standards, from patient protection to regulatory compliance. Because direct part marking plays a key role in ensuring traceability and unique device identification (UDI) conformity, it’s…

David Isaacson
For today’s manufacturers, quality is no longer just a box to check; it has evolved into a strategic pillar central to company success. Once a tactical process focused on meeting regulatory standards, it now plays a leading role in a company’s profitability, brand reputation, employee safety and…

Creaform
Since its founding in 1974, Intercontrôle has been a leader in France’s nuclear energy sector, ensuring the safety of reactor components through automated nondestructive testing (NDT).
As part of the Framatome group, the company develops its own inspection equipment, oversees logistics and…