Content by Joseph Near, David Darais
Tue, 06/15/2021 - 12:02
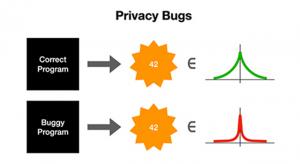
In previous articles we have explored what differential privacy is, how it works, and how to answer questions about data in ways that protect privacy. All of the algorithms we’ve discussed have been demonstrated via mathematical proof to be…
Tue, 05/11/2021 - 12:03
In our last article, we discussed how to determine how many people drink pumpkin spice lattes in a given time period without learning their identifying information. But say, for example, you would like to know the total amount spent on pumpkin spice…
Wed, 04/21/2021 - 12:03
How many people drink pumpkin spice lattes in October, and how would you calculate this without learning specifically who is drinking them, and who is not?
Although they seem simple or trivial, counting queries are used extremely often. Counting…
Mon, 04/12/2021 - 12:03
It’s not so simple to deploy a practical system that satisfies differential privacy. Our example in the last post was a simple Python program that adds Laplace noise to a function computed over the sensitive data. For this to work in practice, we’d…
Thu, 03/25/2021 - 12:03
Does your organization want to aggregate and analyze data to learn trends, but in a way that protects privacy? Or perhaps you are already using differential privacy tools, but want to expand (or share) your knowledge? In either case, NIST’s blog…